SOC Optimization
Test your SOC detection
and response (SLA).
Make sure the front line of your real-time security defense is on-guard.
Improve how your SOC detects attacks with automated tests.
Test how well your SOC is doing and what needs to be better. Help your team focus on the most important security issues.
FAQ
How to test a SOC?
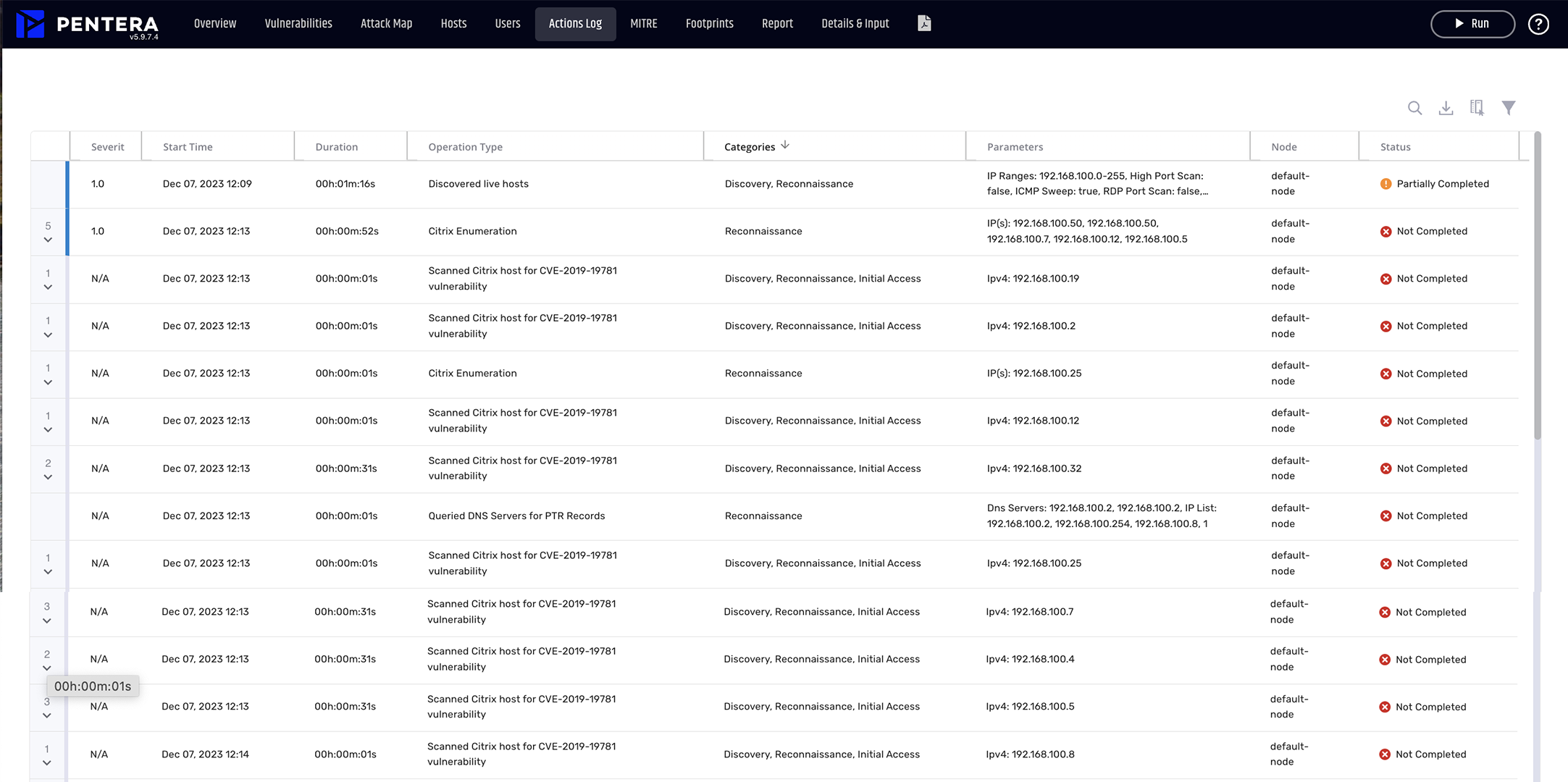
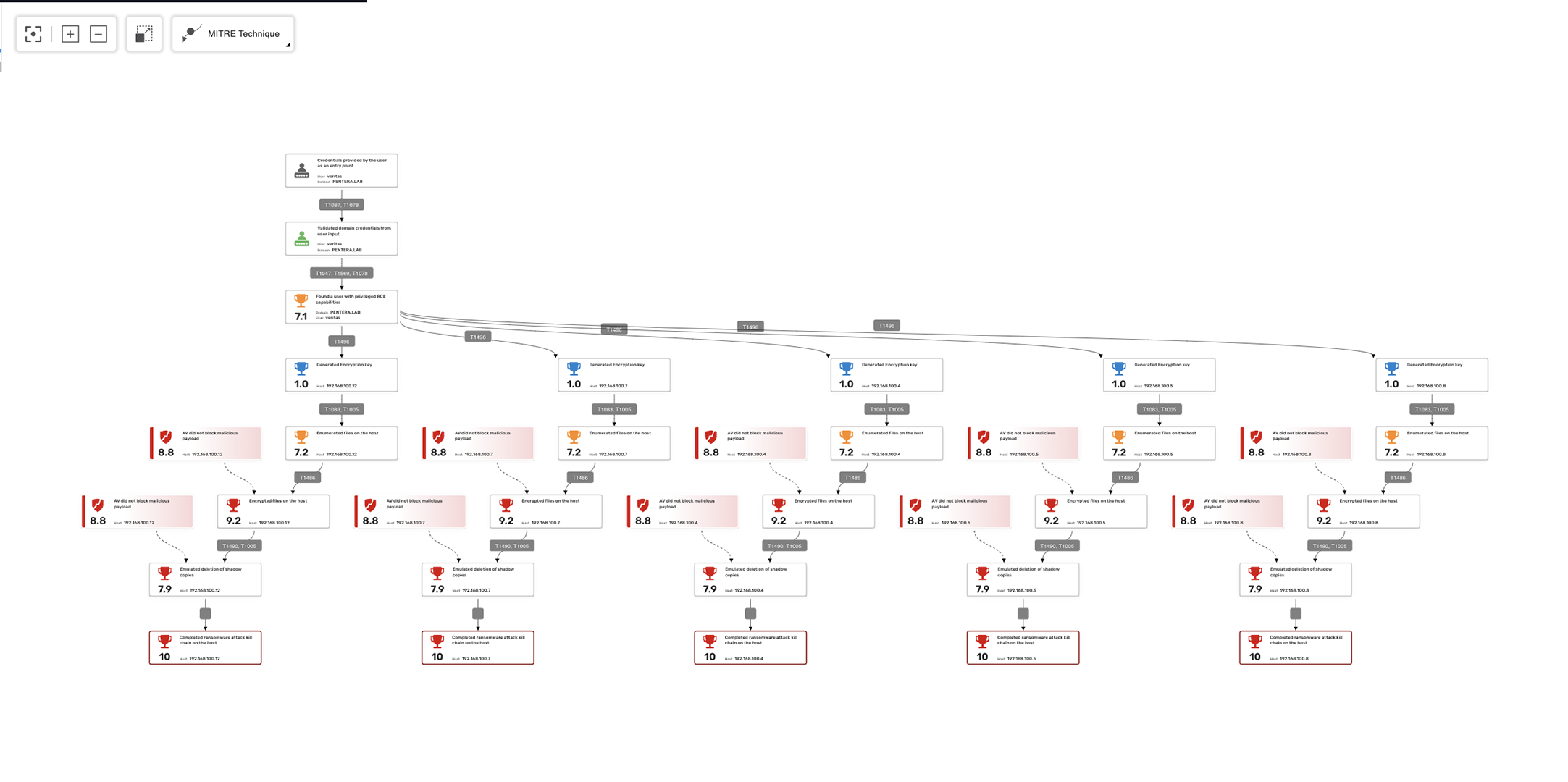
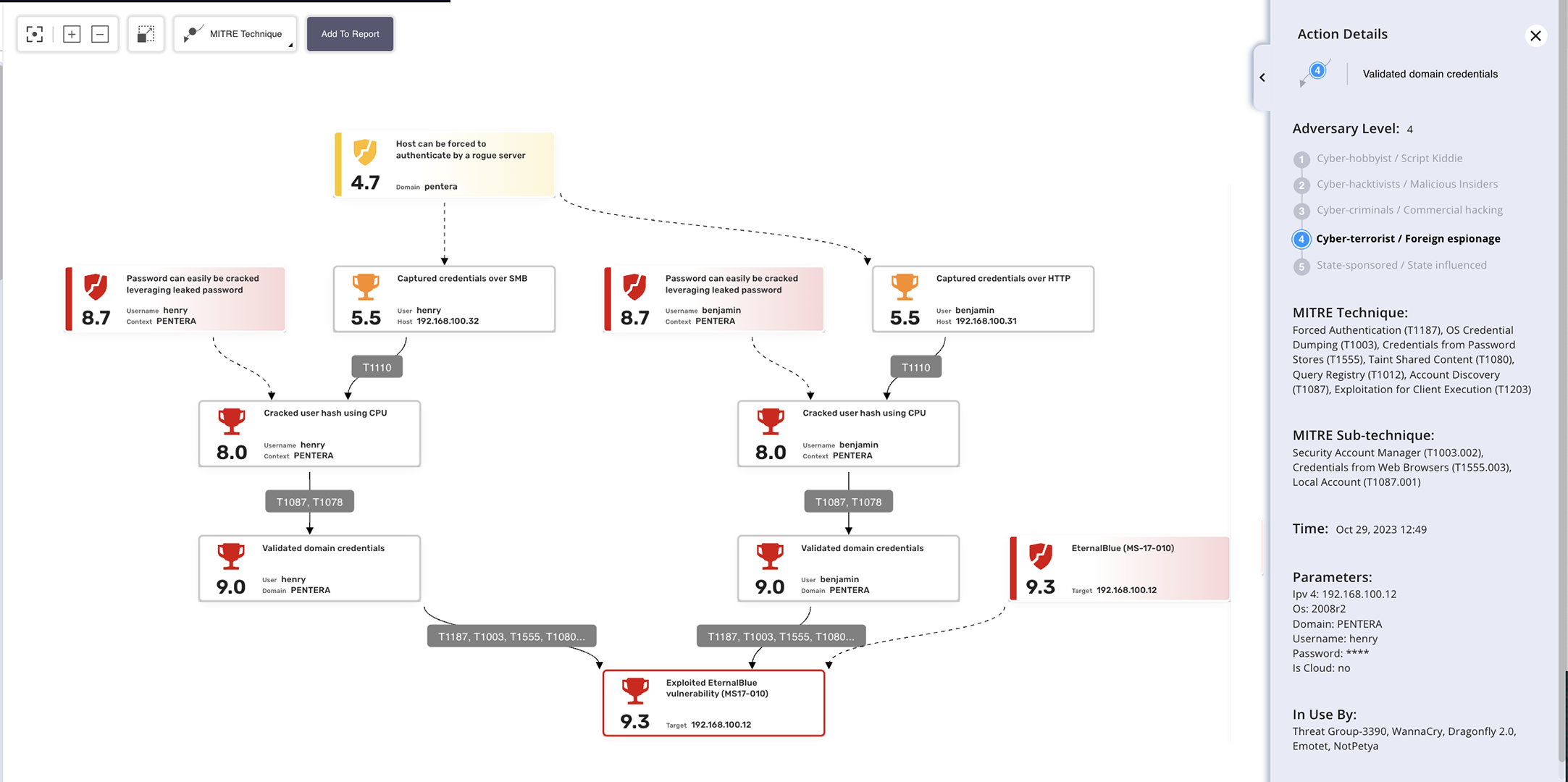
To test a SOC, emulate real-world attacks and observe detection, alerting, and response. This includes validating SIEM rules, alert triage, and incident handling. Pentera automates safe, in-production attack emulation to continuously test your SOC’s ability to detect and respond across the full kill chain.
What are the techniques of SOC testing?
Common techniques include red teaming, breach simulations, log injection, tabletop exercises, and automated attack emulation. Pentera provides scalable, repeatable testing using real adversary tactics to measure SOC detection accuracy, alert prioritization, and incident response readiness.
What is the SOC 2 assessment tool?
SOC 2 assessments are conducted using audit frameworks, often with support from tools like Vanta, Drata, or TrustCloud, to assess security, availability, and confidentiality controls. SOC 2 focuses on compliance, not threat detection. Pentera complements this by validating technical control effectiveness in live environments.
What is the average response time for a SOC?
Average SOC response time varies widely, from minutes to hours, depending on alert quality and team maturity. Response time is often slowed by alert fatigue and false positives. Pentera helps improve this by prioritizing fixes and reducing noise through automated remediation workflows.
What is MTTD and MTTR in SOC?
MTTD (Mean Time to Detect) is the average time taken to identify a threat. MTTR (Mean Time to Respond) measures how quickly the threat is contained or resolved. Pentera helps improve both by generating validated attack signals, allowing SOCs to test and optimize detection and response workflows.