Attack surface monitoring
Ensure your attack
surface is secure.
Never overlook any security gaps in your digital footprint.
Manage your entire attack surface - internal network, web-facing, and cloud.
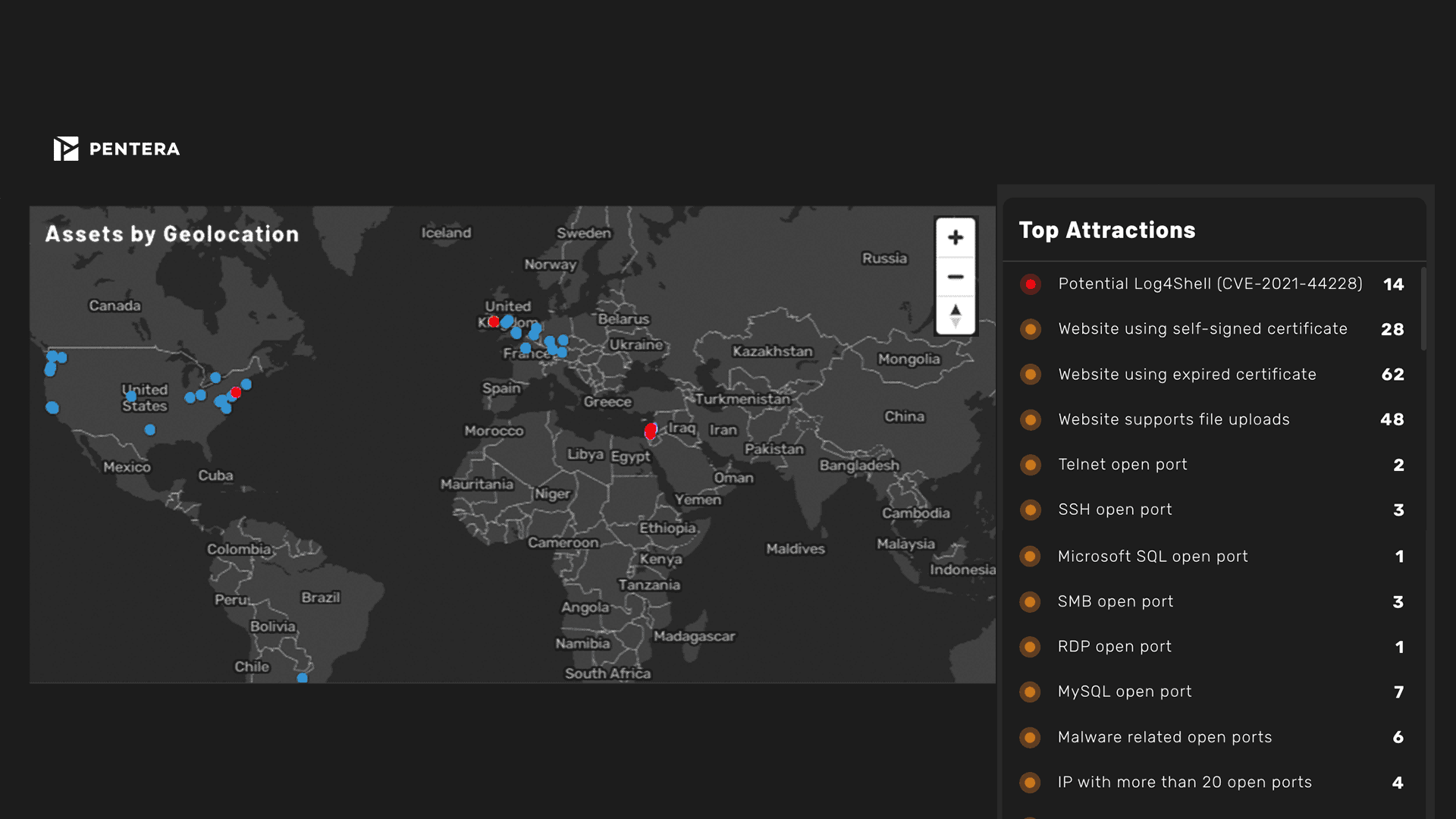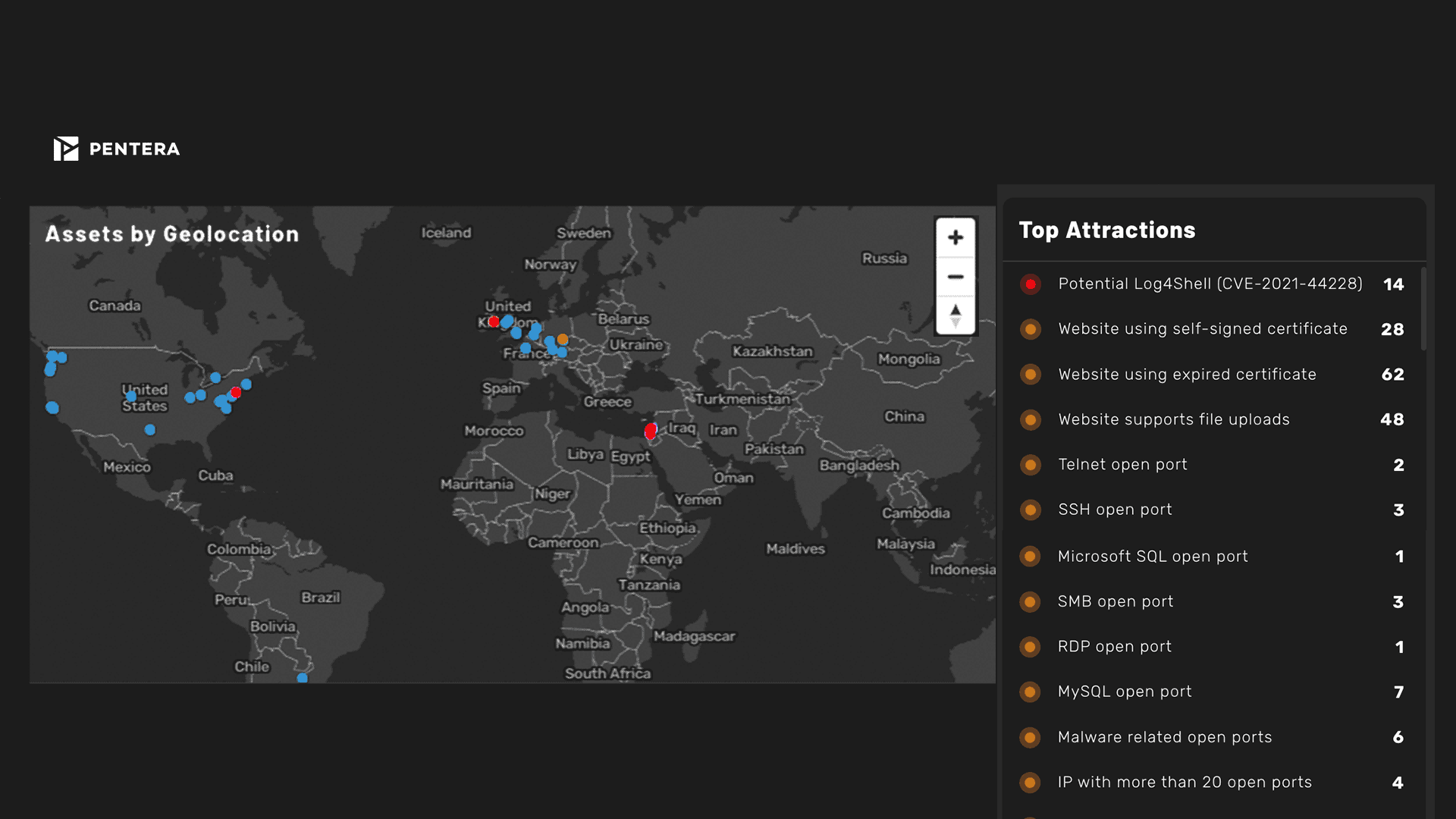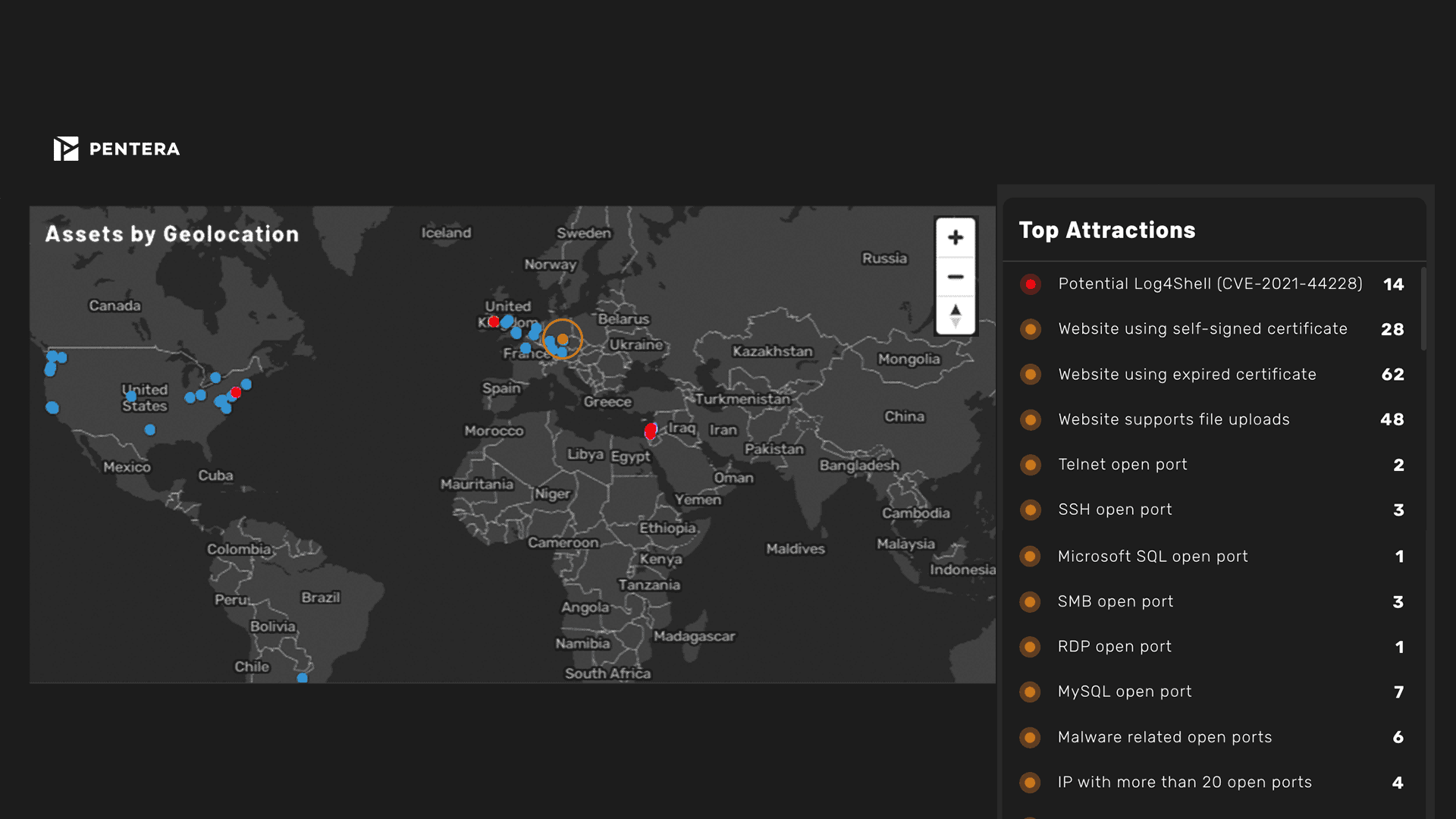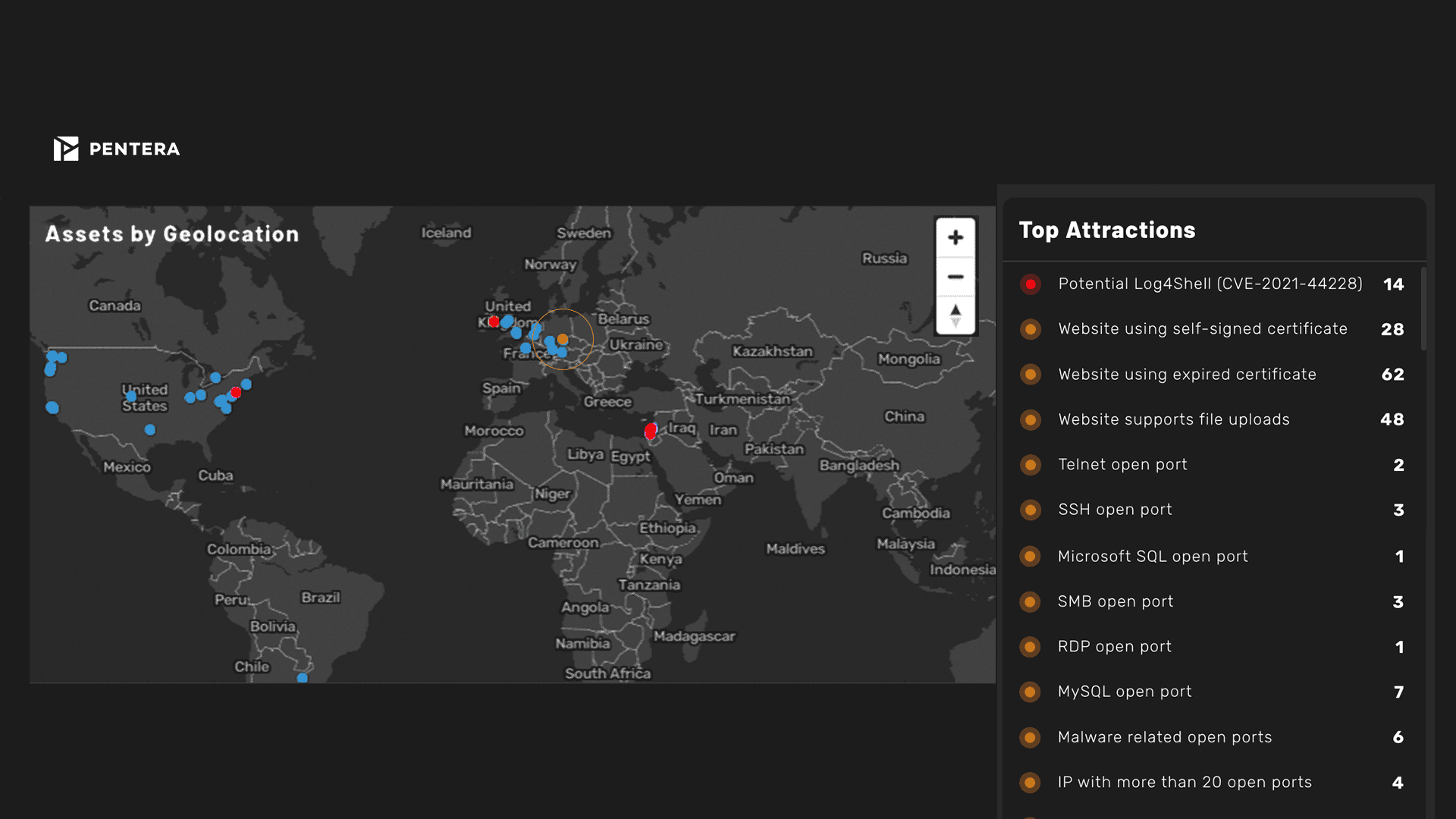
Find out where you are vulnerable by continuously monitoring the security of all your digital assets, including site-to-site testing. Proactively challenge your security controls to see your actual cyber exposure.
FAQ
How do you measure the attack surface?
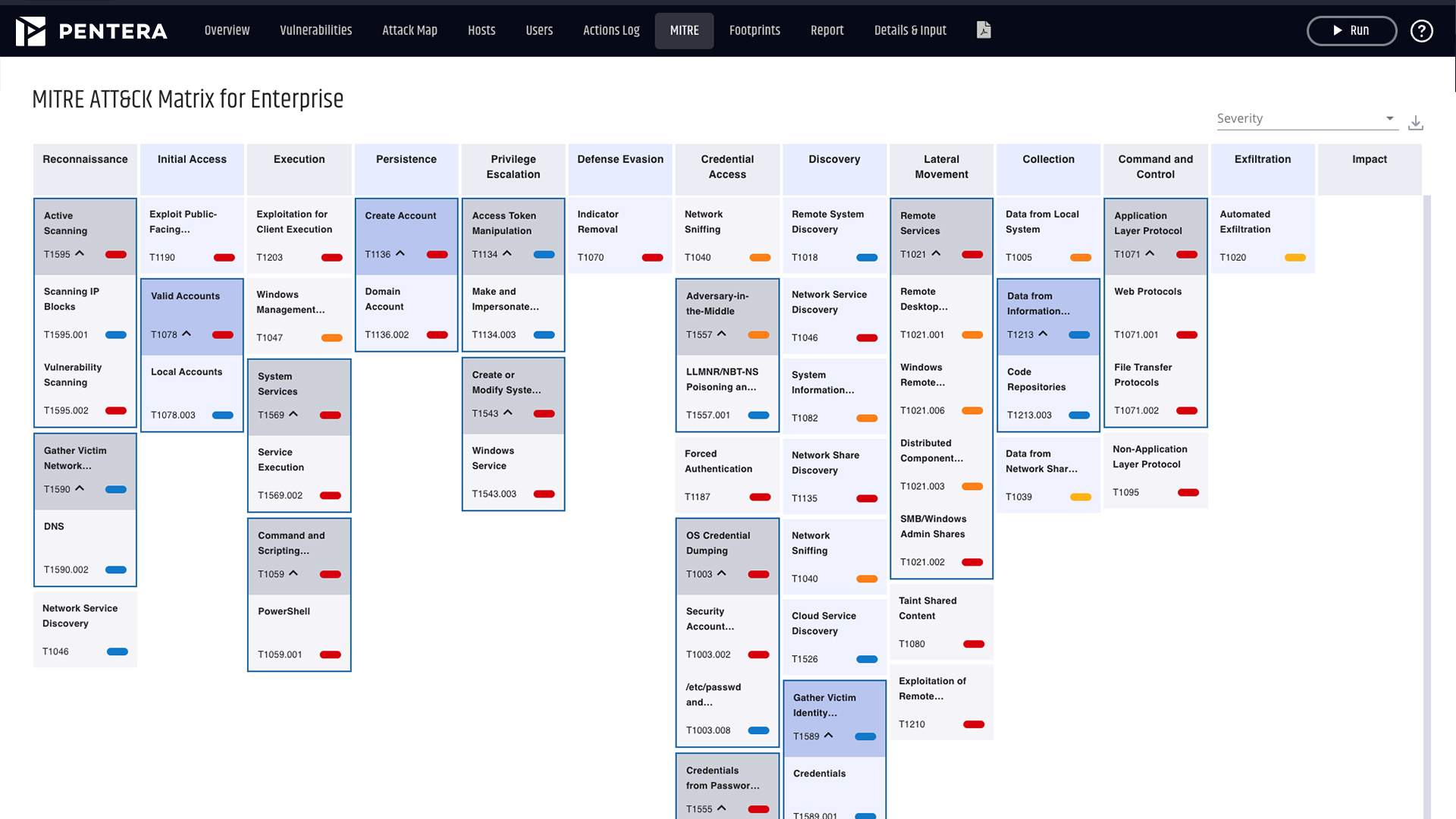
Attack surface is measured by identifying and mapping all accessible assets, internal, external, and cloud, including systems, applications, endpoints, and identities. Key factors include asset exposure, misconfigurations, open ports, credential usage, and potential attack paths. Pentera measures attack surface not just by presence but by proving exploitability through real attack emulation.
What is the primary difference between attack surface monitoring and traditional vulnerability scanning?
Traditional scanners identify known vulnerabilities and misconfigurations. Attack surface monitoring continuously maps and tracks all exposed assets across environments, including shadow IT and cloud services. Pentera goes further by validating which exposures are actually exploitable, providing context beyond static discovery.
What is an attack surface assessment?
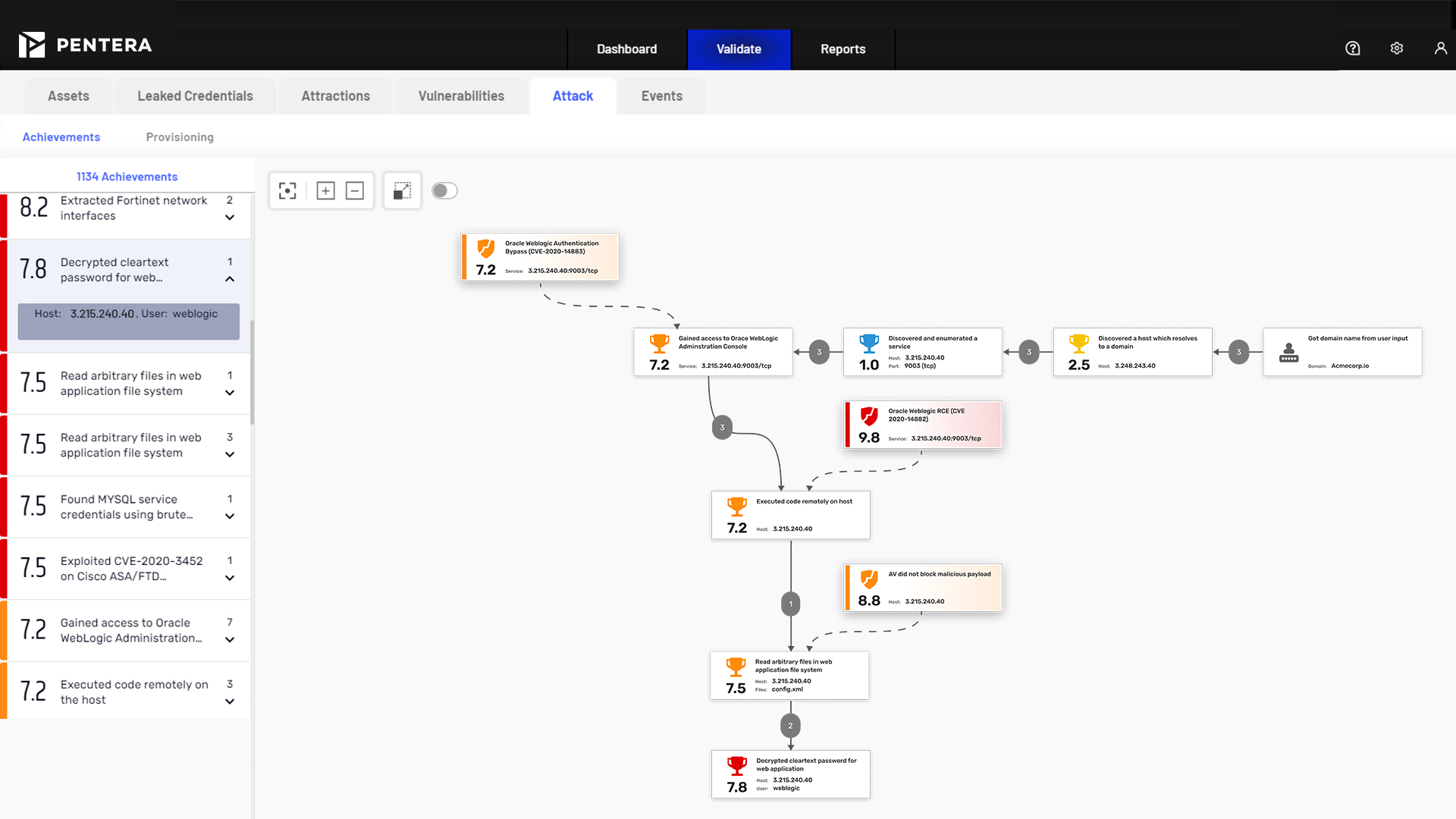
An attack surface assessment identifies all digital assets and entry points exposed to potential threats. It helps security teams understand what attackers see and how they might gain access. Pentera enhances this by safely emulating attacks to assess whether exposures can be exploited.
What is an example of attack surface analysis?
A common example is discovering publicly exposed cloud storage, misconfigured VPNs, or unused domains. Pentera’s attack surface analysis might reveal an exposed S3 bucket that can be accessed and exploited in a kill chain, demonstrating not just visibility but risk.
What technique generally reduces an attack surface?
Techniques include removing unused services, closing open ports, enforcing least privilege, segmenting networks, and regularly validating configurations. Pentera supports reduction by identifying exploitable paths, guiding remediation efforts based on real attacker behavior.