May 24, 2021
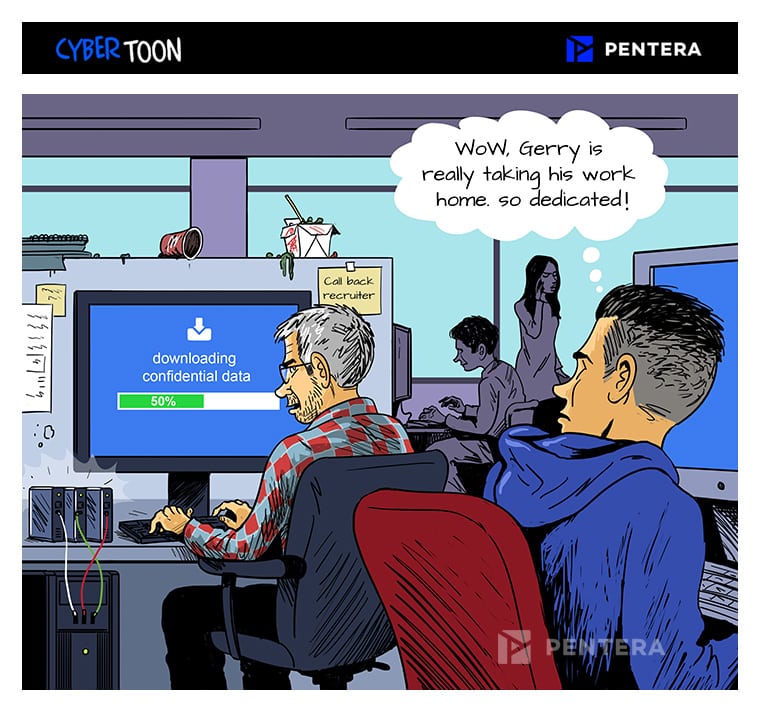
Trust is the basis of society and business. As employees need access to information to do their job, it is impossible to nullify the ability of users to exploit their privileges if they turn rogue.
Users ask for access to more and more assets to do their jobs and the IT departments tend to approve and carry on. With time and employee churn, more-than-intended pools of privilege are created, especially with long-term employees.
The right way of going about it is VALIDATING that your least-privilege policy is concurrent with your least-privilege practice. This needs to happen even if you can’t afford a fully-fledged Privileged Access Management system.
Systemic testing for privilege-sprawl is a new trick for you!? Try Pentera.
<Previous

Red Team Rover
The concept of the game Red Rover is simple – two opposing teams, each with all its players holding hands. They take turns sending one player to “attack” the other side, by finding the weakest link and infiltrating the line – bringing new meaning to “brute forcing” one’s way in. From the “attackers’’ vantage point […]
Next>
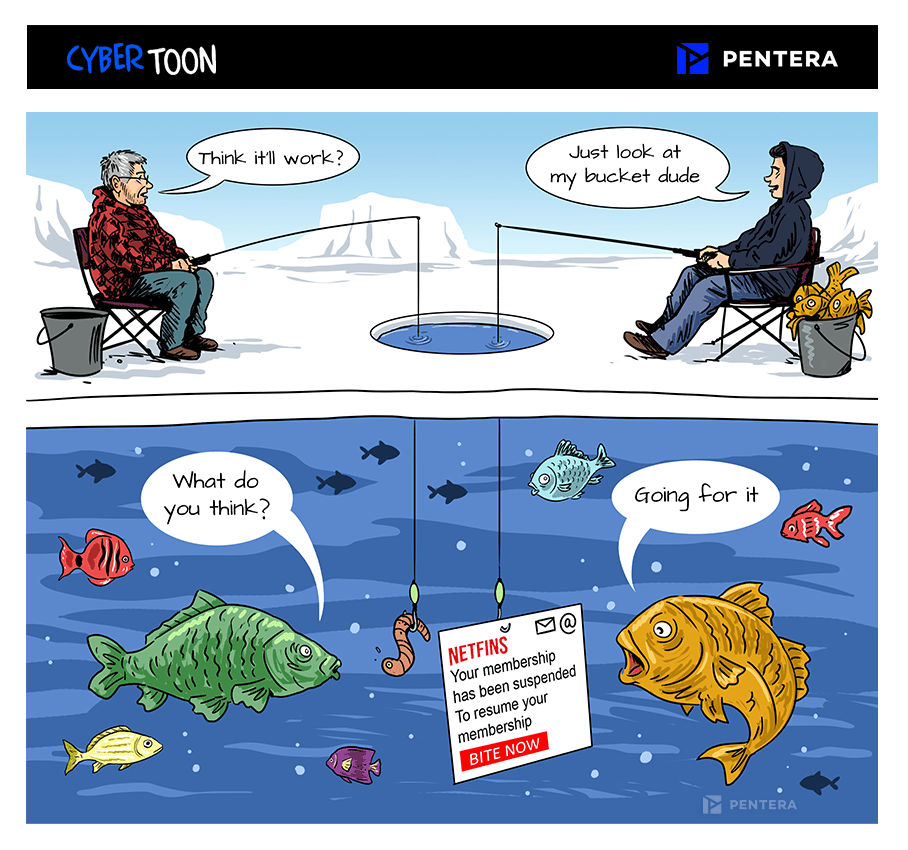
Gone Phishing
Phishing is not going away, it’s evolving. And users? With our current span of attention (9 seconds) and email overload, there is no chance of getting all our employees to be phishing detectives.



